Unleash the Power of Vulnerability Management
Discover, prioritize and manage internal and external vulnerabilities. Harden the networks you manage and protect against evolving threats with vulnerability scanning from VulScan.











Harden Your Network With Simplified Vulnerability Management
VulScan is a powerful tool for complete and automated vulnerability scanning. It detects and prioritizes the weaknesses that hackers can exploit, empowering you to harden networks of any size or type and creating an extra layer of cybersecurity protection.
Uncover hidden internal and external vulnerabilities
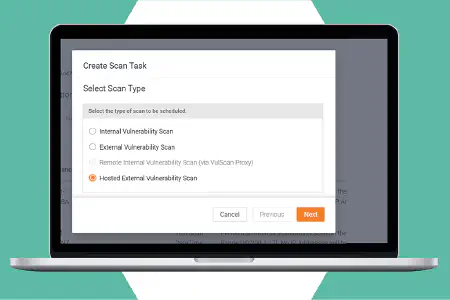
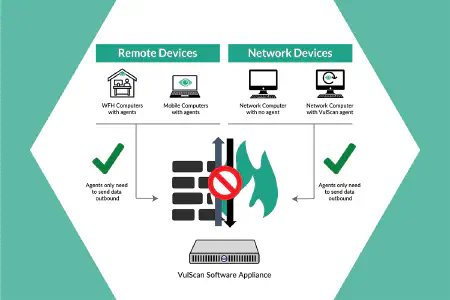
Protect the networks you manage with flexible network scanning options. Vulscan includes on-prem internal network scanners, computer-based discovery agents, remote internal scanning by proxy, and hosted external scanners for comprehensive vulnerability management.
Protect at scale with multi-tenant architecture
Manage multiple network environments at scale with VulScan's multi-tenant vulnerability management platform. With no limits on the number of scanners you can use on each environment, you can manage multiple networks of any size.
Actionable remediation management plans
Take the guess work out of risk management with accurate risk scoring based on severity. VulScan provides expert issue remediation guidance and known solutions available to further speed up issue fixes.
See How VulScan Works
VulScan is the affordable vulnerability scanning solution that works from both inside and outside the networks you manage. It provides the flexibility to schedule scans and filter results for efficient and automated vulnerability management. Access scan results through the user-friendly web management portal. Set up an unlimited number of network scanners using our software deployed on a Docker container, Hyper-V or VMWare; and install discovery agents on target machines to strengthen vulnerability coverage.
VulScan gives you full control over your scanning process to reduce risk and ensure comprehensive protection for your systems.
Take interactive tourVulScan's Vulnerability Management Features
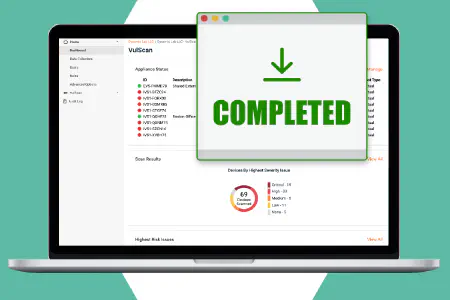
VulScan is an all-in-one solution that uncovers and prioritizes internal and external vulnerabilities in the networks you manage. Quickly flag the most critical vulnerabilities as they appear with its user-friendly dashboards and reports and address them before they can be exploited.
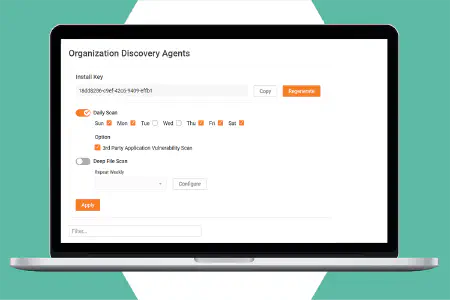
Local and remote internal vulnerability management
Automate full network vulnerability scans to run on any schedule to ensure all network assets are regularly scanned and managed to reduce risk. Options include on-site network scanners, remote internal scanners that you host, as well as individual lightweight discovery agents for Windows machines.
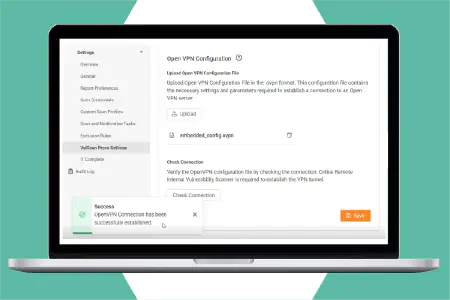
Local and hosted external vulnerability scanning
Set up a scanner on your own remote data center-or any machine outside the target network—to perform external vulnerability scans at multiple locations. Alternatively, access the optional hosted scanner farm for effortless external vulnerability scanning on any site(s) where you perform internal scanning.
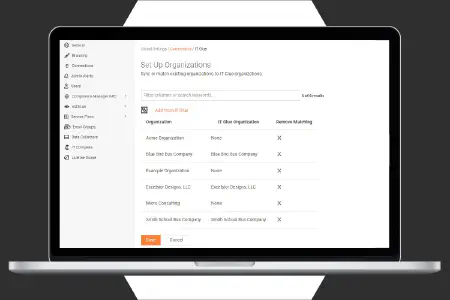
Multi-tenant management dashboard
Manage multiple networks through a single online management portal. Dashboard view displays results for all scans, new and remediated vulnerability trends. Filter the results to prioritize your work and get remediation details for easy and effective management of multiple organizations and sites.
Vulnerability noise management
Reduce alert noise from repeating vulnerabilities by marking them as addressed, false positives or addressed to remove them from dashboards, reports and from future notifications. Multiple criteria can be set, including start and end dates, for greater flexibility when suppressing issues and ensuring that only the important and desired vulnerabilities are presented.
Automatic service ticket creation
Save time and ensure remediation can be assigned properly and tracked in PSA systems. VulScan can automatically create tickets for discovered issues and vulnerabilities in Autotask, BMS, ConnectWise and other PSAs. Create tickets for all issues or just those selected during the review process. Further filter results by severity to get the right resources working on the right issues.
Additional power features
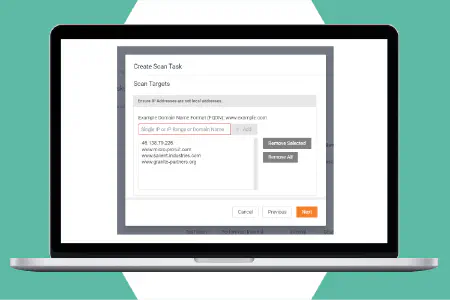
Customize vulnerability scan tasks to target specific IP ranges and TCP and UDP ports during different scans. Run authenticated scans on accounts with credential-secured network endpoints, including computer systems or network devices via SNMP. Attach multiple scanners to the same network to divide the workload and reduce scan time. Scan by IP address, domain name or hostname.
Address Known Network Vulnerabilities With the Right Solution
With over 50 new vulnerabilities discovered every day, no cybersecurity strategy is complete without a plan for vulnerability discovery and management. This guide addresses the most common threats and outlines the tools and processes you need to deal with them.
Download Now
Automated Vulnerability Alerts and Reports
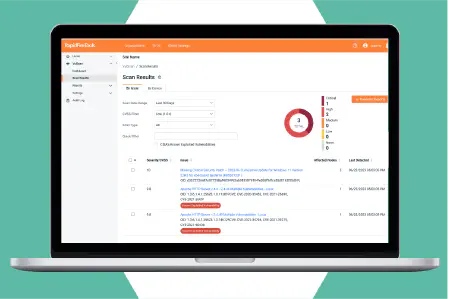
Generate alerts and report output from your vulnerability scans quickly and easily. Use custom filters to focus on the assets you want to include, while screening out issue types, users and CVSS ranges that you want to ignore.
Reports by issue type
Automatically generate reports showing all discovered vulnerabilities organized by type of issue. The report includes all devices that share the same vulnerability, allowing you to apply bulk fixes more efficiently. Includes details about the issue and remediation advice.
Reports by device
Automatically generate reports showing all discovered vulnerabilities on an individual device. For each device listed, the report scores and ranks the issues, giving you the option to address all of them at the same time, or prioritize the work when resources are limited.
Email alerts
Email alerts provide timely notifications regarding completed scans and summary information about the scan results. They help you stay informed about newly discovered critical and high-risk vulnerabilities so you can take quick actions to reduce or eliminate the risk.
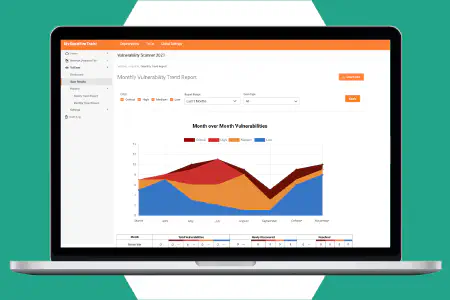
Trending reports
See how your network security posture is changing over time. Trending reports keep a running weekly or monthly tally of newly discovered vulnerabilities-segmented by severity-as well as the number of vulnerabilities that were resolved over the same timeframe.